Journal of Mobile, Embedded and Distributed Systems, vol. V, no. 3, 2013ISSN 2067 – 4074www.jmeds.eu

Figure 2. Internet of Things tech items
The Internet of Things has many applicability
areas and fields, such as the healthcare
sector, the retail sector, transportation
services, educational services, industry and so
on.
Due to the large applicability of Internet of
Things, experts agree that the opportunities
presented by the Internet of Things are
endless, as it becomes easier and easier to
bring physical objects online. A practical
example is represented by different smart
devices connected on a social network for
machines that will help homes to save energy
[1].
Figure 3 presents the simplified schema of IoT
home saving energy example.
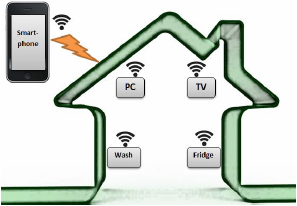
Figure 3. IoT home saving energy example
As we can see from Figure 3, the online
network of physical objects is realized by using
RFID tags and some other types of sensors.
By implanting these tags inside a physical
object, the object gives the power to be
monitored and controlled remotely through the
Internet, with the help of a smartphone. This
eliminates the need for human people to
constantly enter and monitor data. Instead,
objects can work directly with each other and
can collaborate without the need for a person
to link them together [2].
3. Smart Tags/Cards for Things Authentication and Data Integrity
In a retail or supply chain management
integrated solutions, RFID – vicinity/proximity
tags or cards will be attached to the products
and things, in order to store data and metadata about the products. The sensors will
read or modify the data stored in RFID labels
attached to the things. In order to provide
authentication and data integrity, the solution
will have an authentication procedure that
requires minimum of processing and power
consumption, but in the same time it will be
strong enough to avoid security pitfalls.
The minimum authentication model will require
a mechanism similar with CRYPTO1 from
Mifare 1K/4K proximity cards and a higher
secure model would be inspired from Sony
FeliCa cards and VISA/Mastercard DDA
(dynamic authentication) procedure from
banking cards (MULTOS or Java Card).
Mifare DESFire tags/cards have only
contactless interface for communications and
they are fully compliant to the ISO/IEC14443A
(1-4). They have 7 bytes UID (“Double Size
UID”) and from point of view of CPU & OS,
there are the following features:
126
- ↑ Chad Brooks, The Internet of Things: A Seamless Network of Everyday Objects, Available at: http://www.livescience.com/38562-internet-of-things.html
- ↑ Ibid.
